Abuse Desk Notes
Our Abuse and Email Deliverability team's unofficial blog and update site. Many of our twitter posting may link here and we provide followers with current news and information we come across. Information provided here is "as is". While we try to select accurate sources, information comes in fast, and may not always be verifiable.
Monday, September 20, 2010
F-Secure on how to "un-Google" yourself. Privacy tips for the paranoid!
Check out this article from the Safe and Savvy blog about how to limit what information Google can use when you are on their services/sites.
Wednesday, July 28, 2010
Facebook Data Harvested to Build List of Likely Logins
This list was then used to determine the likely variations of "first initial last name", "first name last initial" and so on, which could be helpful at increasing the success of users attempting to log in to systems using brute-force tactics.
The details of how this was done are available at: http://www.skullsecurity.org/blog/?p=887
Monday, July 19, 2010
Security Secrets the Bad Guys Don't Want You to Know
From the article:
"You already know the basics of internet security, right?
You know to keep your antivirus program and patches up to date, to be careful where you go on the Internet, and to exercise online street-smarts to resist being tricked into visiting a phishing site or downloading a Trojan horse.
But when you've got the basics covered, but you still don't feel secure, what can you do? Here are a few advanced security tips to help you thwart some of today's most common attacks.
Remember, however, that security is all about trade-offs. With most of these tips, what you gain in security, you lose in convenience. But hey, it's your computer. Be as paranoid as you want to be."
Thursday, July 1, 2010
Scareware/Rougeware Propogation Tactics
The infection routines being used by some scareware and rogue AV gangs are much more comprehensive and far-reaching than many current analysis have shown
Quote from SANS -
""Once the site has been compromised, the attackers install their script in any directory, preferably in a directory that is not accessible directly from the web since they will not need to access it directly. The next step the attackers do is to infect all (and I mean all!) PHP files on the compromised web site. If it's a shared web site, and the permissions are not setup correctly, they will actually infect absolutely every web site hosted on that machine,"
Read the full article and Threatpost
Saturday, June 5, 2010
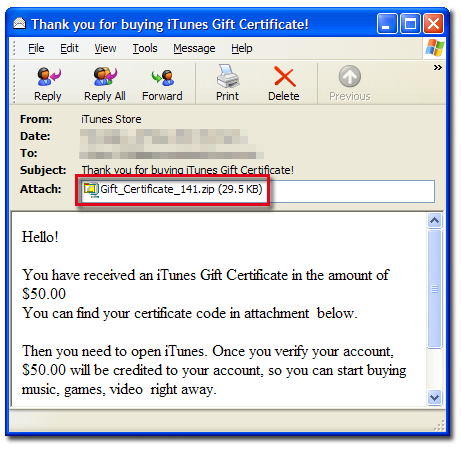
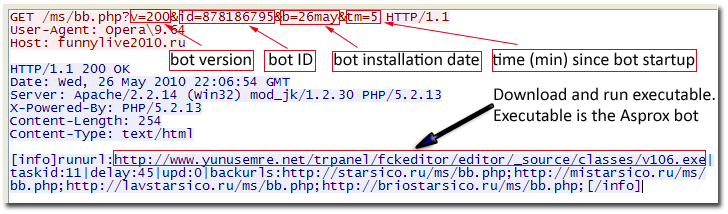
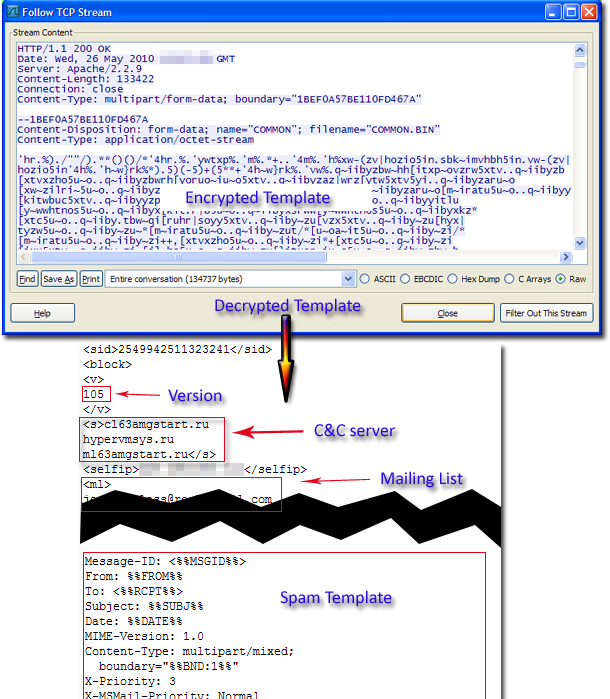
The Asprox Spambot Resurrects (apparently with some new tricks)
"With the help of Pushdo and Bredolab downloader, it seems Asprox has risen from the dead to build another spamming bot network. The above analysis also highlights the intricate relationships between individual malware components, and hint at a common gang behind it all."
Thursday, June 3, 2010
Stable release of Firefox 3.6.4 delayed
The development of browsers that "sandbox" or isolate historically problematic plugins and processes is encouraging. Look forward to seeing how this changes development of other apps that are reliant on external programs.
RC for this release can be found here
NetMarketshare's OS report
Here is the current month -
One of the things that stood out to me was the number of mobile devices/OSes captured from last years reports in June (e.g. iPhone from .20 to .60%).
Wednesday, June 2, 2010
McAfee - Interesting look at common "exploit packs" and target vulnerabilitites
Very interesting look at the kits and what well-known exploits they go after -
Check out McAffee's blog post for other images from these kits and their very informative write-up (including prices) on this.
Mac users get own their version of a Windows Spyware variant
List of applications known to contain this malicious code -
- Secret Land ScreenSaver v.2.8
- Color Therapy Clock ScreenSaver v.2.8
- 7art Foliage Clock ScreenSaver v.2.8
- Nature Harmony Clock ScreenSaver v.2.8
- Fiesta Clock ScreenSaver v.2.8
- Fractal Sun Clock ScreenSaver v.2.8
- Full Moon Clock ScreenSaver v.2.8
- Sky Flight Clock ScreenSaverv.2.8
- Sunny Bubbles Clock ScreenSaver v.2.9
- Everlasting Flowering Clock ScreenSaver v.2.8
- Magic Forest Clock ScreenSaver v.2.8
- Freezelight Clock ScreenSaver v.2.9
- Precious Stone Clock ScreenSaver v.2.8
- Silver Snow Clock ScreenSaver v.2.8
- Water Color Clock ScreenSaver v.2.8
- Love Dance Clock ScreenSaver v.2.8
- Galaxy Rhythm Clock ScreenSaver v.2.8
- 7art Eternal Love Clock ScreenSaver v.2.8
- Fire Element Clock ScreenSaver v.2.8
- Water Element Clock ScreenSaver v.2.8
- Emerald Clock ScreenSaver v.2.8
- Radiating Clock ScreenSaver v.2.8
- Rocket Clock ScreenSaver v.2.8
- Serenity Clock ScreenSaver v.2.8
- Gravity Free Clock ScreenSaver v.2.8
- Crystal Clock ScreenSaver v.2.6
- One World Clock ScreenSaver v.2.8
- Sky Watch ScreenSaver v.2.8
- Lighthouse Clock ScreenSaver v.2.8
Tuesday, May 25, 2010
Microsoft continues uphill battle against the Alureon rootkit
"Almost two-thirds (65%) of the PCs infected with Alureon this month were running Windows XP Service Pack 3 (SP3), with the No. 2 spot taken by Windows XP SP2 (14%). Only 3.5% of the rootkit-infected PCs were running Windows 7, said Microsoft."
Have to give Microsoft credit for not giving up on this. The longer this problem persists, the longer these machines stay vulnerable. They are aiming at an unpredictable, moving target though.
Devious New Phishing Tactic Targets Browser Tabs
Some good news is that users running NoScript, Safari or Chrome don't seem to be affected by these iterations of the attack.
Example of concept is here
Thursday, May 20, 2010
Present Day History of Conficker
Wednesday, May 19, 2010
New Rogueware links identified in many popular entertainment related search queries
The distributors have been observed achieving very high search rankings for queries on the following topics:
Lost episodes
Friday Night Lights
The Boondocks
The Hills
Family Guy
Iron Man 2
Misc. Popular Musicians
Death of Ronnie James Dio
.. and others
Panda Labs describes the software as:
"MySecurityEngine is an adware program that deceives users warning them of unexisting threats in their computers so that they purchase a certain program that removes them from the computer.
Additionally, it prevents users from accessing certain search engines and from running certain security programs, like antivirus solutions, firewalls, or even fils belonging to fake antivirus programs. It also modifies the searcher that is displayed in the Search option of the Internet Explorer browser.
MySecurityEngine can reach the computer in spam messages containing a link or an attached file, or through malicious websites that have obtained googd positions in the search engines by using BlackHat Seo techniques"
File-sharing can be risky business!
There are many free or inexpensive ways to consume high-quality media online such as Centurylink Video Store, CenturyLink Unlimited Music (and videos), Netflix, iTunes, Hulu and others.
Using reputable services like these can provide great content and save a lot of frustration.
Tuesday, May 18, 2010
New and improved Zueskit payload from spam messages
"for instructions and an executable that is meant to be the patch to apply. The executable file named adbp932b.exe (SHA1 0632f562c6c89903b56da235af237dc4b72efeb3) has minimal coverage of about 7%."
Monday, May 17, 2010
Facebook Privacy Check - From the F-Secure Blog
Try this interesting app to see what the privacy and security footprint of your Facebook profile really looks like. It may surprise you!
We'll try to add some discussion about social networking (from both sides of the field) and specifically the recent changes to Facebook in our next webcast.
Phishlabs baits a phisher (and reports some great insight)
The fact that this type of activity is now being made available to mainstream opportunists is a double-edged sword. While the prevalence is increasing, it allows allows researchers more opportunities to capitalize on amateurs making mistakes. This was just one such case.
This SC based research organization found this phisher's "back door" and watched it.
AS50896 - (PROXIEZ) Gets Taken Offline
Increased risk (and potentially higher operating costs) drastically changes the equation for online fraudsters and provide deterrent that has been lacking in the past.
As a "double whammy" today, I'm including a video of yet another Romanian Law Enforcement agency taking a group of scammers into custody.
Saturday, May 15, 2010
"Sexiest Video Ever" on Facebook is a front for Malware
Adding this to your profile puts you and your friends in jeopardy. Please don't follow these links!
"When clicking on the "video" you are taken to an application installation screen asking you to allow it to access your profile, wall etc. Once approved it claims you have to download an updated FLV Player to view the video and promptly sends an EXE your way...
This is the Hotbar Adware which displays ads in your browser based on your browsing habits etc. In addition, the Facebook application just installed will post messages on your friends wall on your behalf with the same "sexiest video ever" message."
Monday, May 10, 2010
Attack Method Bypasses Anti-Virus
Tuesday, May 4, 2010
US Treasury Websites Serving Malware
Wednesday, July 8, 2009
On-going Denial of Service (DDoS) Against US Sites
More information available from F-Secure:
Lyzapo DDoS attack on US and South Korean websites
Wednesday, July 1, 2009
Message Labs spam traffic analysis
- 90% of all email was spam
- 83.2% was botnet generated
- 45% of botnet generated spam appears to be from Cutwail
- Although one of it's main distribution channels was shut down earlier this month, this botnet showed great resilience by getting right back up. Very little reprieve was seen in traffic
- Virus infected emails 1:269
- Phishing emails 1:280
That's a lot of badness floating around out there. Article Here
Friday, June 26, 2009
Security Researchers Claim to Have Located Dropbox with High-profile FTP Logins
Interest attack attempting to use security software update
The email message is:
“Download latest virus identity (IDE) files
If you are running an older version of Sophos Anti-Virus and do not automatically update your protection, you should download virus identity files (IDEs), which provide detection and disinfection of viruses, worms, Trojans and spyware.
All the IDEs you need are available in a single compressed file. NOTE: Please RUN the application accordingly.”
Additional details in the article
General phishing email reported 6/25
Origin -
85.25.132.91
NetRange: 85.0.0.0 - 85.255.255.255
CIDR: 85.0.0.0/8
NetName: 85-RIPE
NetHandle: NET-85-0-0-0-1
Received: from uf5.cybercity.dk (uf5.cybercity.dk [212.242.42.163])
by smtp2.cybercity.dk (Postfix) with ESMTP id 04DDC313CC2;
Thu, 25 Jun 2009 19:07:31 +0200 (CEST)
Received: from webmail.telenor.dk (localhost [127.0.0.1])
by uf5.cybercity.dk (Postfix) with ESMTP id 840D4205D31;
Thu, 25 Jun 2009 19:07:29 +0200 (CEST)
Received: from 85.25.132.91
(SquirrelMail authenticated user onlineid2@mail.telenor.dk)
by webmail.telenor.dk with HTTP;
Thu, 25 Jun 2009 19:07:30 +0200
Dear mail subscriber,
We are currently verifying our subscribers email accounts in
order to increase the Efficiency of our web mail features.
We are deleting all unused Web Mail account,
To confirm your account is currently in use and join in the
Recent Upgrade Taking Place,
You must Reply to this email by Providing your email Password
in the blank space below. Failure to do this will immediately
render your email address deactivated from our database.
Confirm Your Web Mail Login information
:::::::::::::
FIRST AND LAST NAME:
USERNAME:
PASSWORD:
:::::::::::::
Attention! Account holder who refuses to update
his account within Seven days after receiving this warning will
lose his account permanently.
Thanks for using Web mail
WebMail Admin System
Warning Code :UCIX782X
Several links and info on Twitter devleoping as target for attackers
According to the article
The new component uses a victim’s Twitter account to post tweets using Internet-browsing cookies to log in to the target user’s account. Tweets can more successfully be posted when the victim is currently logged on to his/her Twitter account as the ‘evil’ Koobface binary runs in the background.
The content is allegedly updated from a C&C server and then uses shortened URLs from Tinyurl.com to further obfuscate the threat.
In other big Twitter related attack news this week, Sophos has posted a video showing exactly how Guy Kawasaki's feed was exploited and used to try to propagate malware. It's interesting that they used a Mac to show how this exploit worked.
### Warning, this video shows the researcher going to the exploit site which contains erotic imagery which may be offensive or inappropriate in some environments ###
The link to the video is located HERE
Thursday, June 25, 2009
Dangers of auto "redistributing" data and Mac Malware updates
Full article Here
Great analysis and update on the inner workings of "Nine Ball" Attacks
We just picked up two samples that appear to be part of this last night.
Well worth the read in the threatfire blog HERE
Tuesday, June 23, 2009
4 Guilty Pleas in Spam Ring Prosecution
Brian Krebs of the Washington Post has an article (photos courtesy of Spamhaus) covering the guilty pleas of four individuals involved with what is described as "on of the worlds top spam kingpins".
The complete list of those pleading guilty of involvement and associated charges:
- Scott K. Bradley - Up to 87 months in prison and $1,000,000,000 fines
- John Bown - Up to 63 months in prison and $75,000 fine
- William Neil - Up to 37 months incarceration and $30,000 fine
- James Fite - 2 years incarceration and $30,000 fine
Sentencing is scheduled for 29 Oct, 2009
Full article is HERE
Your PC "for rent"
There are attached whitepapers covering the following
- On the buyer side of the trading platform, batches of 1,000 malware-infected PCs can be purchased for $5 up to $100; depending on territory
- Partners are paid for successfully distributing the bot and collecting FTP-credentials of legitimated websites through the infected PCs
- On the seller side of the trading platform, cybercriminals sell batches of 1,000 malware-infected PCs for $25 up to $500
- Compromised malware infected PCs may be infected with additional malware each time they are purchased by a new "owner"
- For attacks and exploitations, an exploit toolkit with obfuscated code and the Trojan Zalupko attack toolkit are provided
Very interesting and easy to follow article about a fairly standard botnet.
Monday, June 22, 2009
Very simplistic and hard to mitigate DoS for Apache Servers
Some recommendations for protecting against this type of attack are HERE and HERE, but there may be some impacts on "normal" usage as well.
Sunday, June 21, 2009
Some discussion on new Virut activity from Threatfire research
Hosting company loses user data due to zero-day exploit
Cybercrime gets more accessible
Saturday, June 20, 2009
Two new malware attacks against Mac users
Also noteworthy aside from the fact that these target the Mac user base (which is normally considered to be a less valuable target to attackers due to the smaller user base) is the fact that the authors are using adult content websites for propagation. There has been a declining trend of this on the spam scene over the past couple years.
Nice articles from Cloudmark on Deliverability Issues
Part I Some Background
Part II Basic Steps and Information to get if you are blocked
If these steps don't work, contacting the Abuse Desk or deliverability manager for the "blocking party" should get the issues resolved.